ABOUT OUR PROJECT
In 2013, Edward Snowden's revelations about the NSA's surveillance of Americans radically changed how we view privacy in our digital world. However, six years later, the average user of technologies such as cell phone calling and text messaging puts little to no thought as to whether their calls or texts are being recorded and stored in government databases. Therefore, we are setting out to investigate the origins of government, technology-based surveillance, the technical aspect of how our calls and texts are being recorded, the legal justifications for surveillance utilized by the government, the legal and ethical implications of surveillance, the role that private corporations play in collecting user data, and the possible positives of government-based surveillance.

Edward Snowden
The inspiration of our project, Edward Snowden, is a whistleblower who copied and leaked highly classified information from the National Security Agency in 2013 when he was a Central Intelligence Agency employee and subcontractor.
Picture courtesy of Laura Poitras

Protests Against Surveillance
According to a survey we conducted, over 90% of respondents feel that the U.S. Government possibly or definitely collects/monitors their data.
Picture courtesy of Fibonacci Blue
GOVERNMENT SURVEILLANCE: THE BASICS
What is the NSA?
The NSA is the National Security Agency. It was founded on November 4th, 1952, and has historically been used for controversial purposes, such as spying on anti-war activists during the Vietnam War, collecting cell-phone data after 9/11, and spying on American citizens through seemingly innocuous website data.

Picture courtesy of NSA.gov
What is the USA PATRIOT Act?
The USA PATRIOT Act was created following the terrorist attacks of September 11th, 2001. This act allowed various government agencies, such as law enforcement, intelligence agencies, and national security agencies to share data with one another. The law also alllows law enforcement to get warrants in any jurisdiction where terrorism has occurred, conduct investigations without informing the suspect, and conduct electronic surveillance of suspects without their consent.

Picture courtesy of library_mistress on Flickr
In what other ways does the government use surveillance?
As of 2019, the Trump Administration has urged lawmakers to reauthorize the USA Freedom Act, which allows the NSA to access logs of Americans' domestic communications. The Administration is also seeking to permanently extend three authorities primarily used by the F.B.I.: one which allows the organization to collect business records, one which allows them to wiretap "lone wolf" terrorists, and one which allows the organization to keep wiretapping individuals who switch their phone line to avoid surveillance. Immigration and Customs Enforcement (ICE), also has access to 1.5 billion data points contributed by 80 law enforcement agencies across the United States as well as license plate data through a contract with Vigilant Solutions.

Picture courtesy of the official ICE Website
MORE ON THE USA PATRIOT ACT
How it's used
Section 215 of the USA PATRIOT Act allows the government to collect electronic searches of any and all United States citizens without probable or reasonable cause.

Picture courtesy of Lianhao Qu on Unsplash
Is the USA PATRIOT Act stil relevant?
Absolutely, as the PATRIOT Act is still effective. In fact, three of its most dangerous provisions were reauthorized as of November 2019: Section 215, which authorizes the government to look into the private records of Americans, the lone wolf provision, which allows the United States to conduct surveillance on non-US citizens with no proven connections to terrorism, and the provision which allows the United States government to use roving wiretaps.
Picture courtesy of Igor Kisselev via Shutterstock
What are its ethical implications?
The PATRIOT Act has been unethical since its inception. The Act authorizes the government to access any and all communications of American citizens online, and has even been used to conduct surveillance against individuals who are not American citizens or who live abroad. The indivuals most frequently targeted by the PATRIOT Act are people of color, especially those who also identify as Muslim.
PATRIOT ACT TIMELINE

SURVEILLANCE CAPITALISM
Terms and Conditions
Our survey results support the claim that a majority of internet users do not read terms and conditions. A common belief is that if a service or website has terms & conditions it is credible. This is false. Terms & conditions may include provisions that you disagree with or that violate your privacy. Without reading them it is impossible to know what you have agreed to.
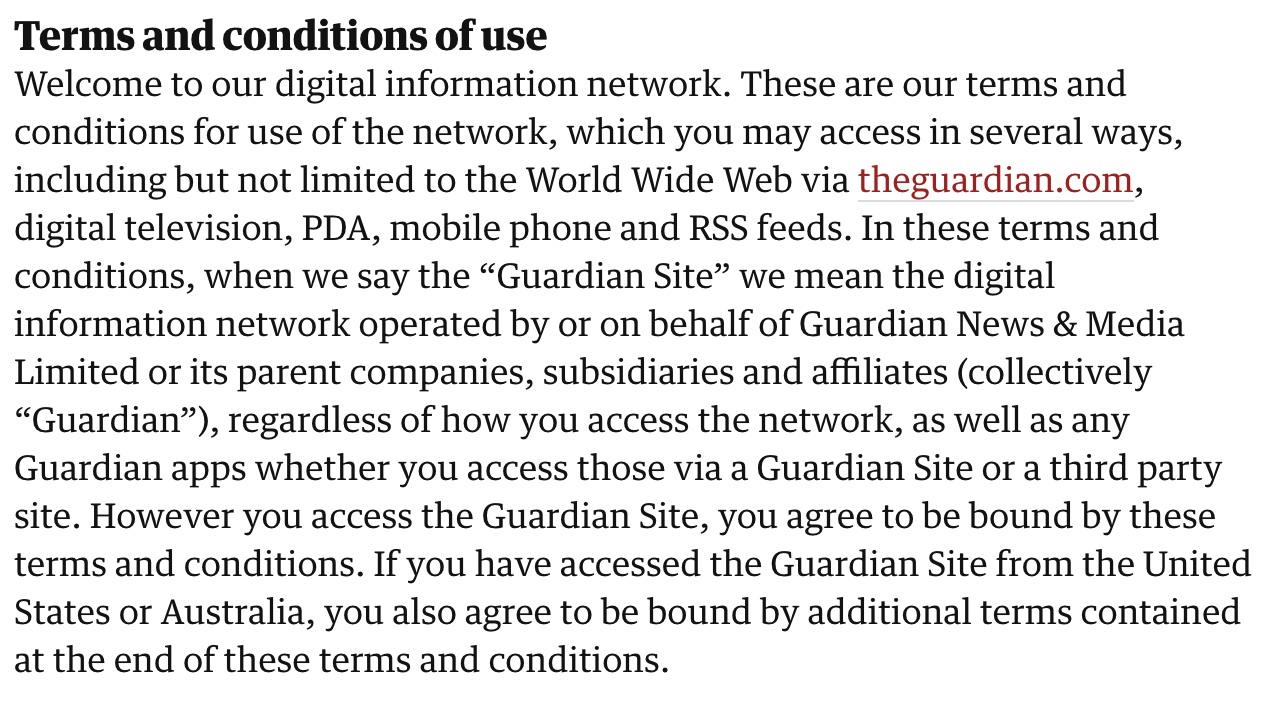
This image displays just the introduction of the terms and conditions of The Guardian's web site. There's many more pages where that came from.
Picture courtesy of The Guardian
VPNs
VPNs are Virtual Private Networks. Using a VPN is a a way to add an extra layer of privacy to your activity on the internet, especially when using public WiFi networks, which are particulary vulnerable to hackers. VPNs encrypt your data and make it harder for a hacker to access your sensitive information by routing all your activity through a separate server.

Picture courtesy of Petter Lagson on Unsplash
Corporations
Companies like Facebook, Google, and Twitter recieve tens of thousands of requests per year from U.S. law enforcement agencies. These companies have control over how easy or difficult they make it for law enforcement to get information. For example, after 9/11, AT&T went above and beyond the information they were required to give the NSA by creating a program to give them as much information on the internet as possible. On the other hand, after information about NSA surveillance was revealed by Edward Snowden many companies have resisted warrants requesting information from the U.S. Government.

Picture courtesy of the official AT&T website
Private contractors are integral to the way internet surveillance is carried out. These contractors are private for-profit companies that work with and for government agencies. Through outsourcing private contractors doing the dirty work for federal agencies. A fifth of full-time staff at government agancies are private contractors. This means less oversight and focus on accountability. The number one goal for private contractirs is profit. They are beholden to stockholders first, not the American people.
The Technology Behind Surveillance
Surveillance can be done on the internet by collecting metadata, logs of phone calls, text messages, social media data, and other private information. Additionally, monitoring is also carried out using facial recognition cameras and aerial surveillance.
5G was supposed to make it more difficult for hackers to get information but it may still be vulnerable to certain attacks. Stingrays or ”IMSI catchers” can trick a device into thinking they are real cell towers and then track the device or listen to phone calls. 5G was supposed to make these attacks impossible. Devices are rated 1 to 12 on complexity. Only devices with higher numbers can connect to 4G/5G. Stingrays are able to change this number and downgrade devices so they cannot connect to 5G where more protections are in place, making information easier to steal.
But we haven't answered probably the most pressing question you have: how did the NSA domestic spying program work? Although much of the technical information remains classified, we can piece together some clues from the work of whistleblowers, and government officials, and journalistic investigations, according to the Electronic Frontier Foundation. The details of every American's call history didn't take much "hacking" to obtain: they merely collaborated with private telecommunications companies, which handed over "call-detail records" of their customers. These same companies also allowed the NSA to install surveillance equipment in secret rooms at these facilities, allowing the NSA to listen to any communication they wanted in real-time. The equipment that made this surveillance possible were called fiber-optic splitters, which make duplicates of the data that pass through them. On a larger scale, machines such as the "Narus Semantic Traffic Analyzer" could conduct deep packet inspection, again duplicating the information transmitted through the network and forward that information to the NSA.

Picture courtesy of Hackaday
HOW TO PROTECT YOUR PRIVACY ON THE INTERNET
Why protect it in the first place?
We hope that reading our webpage up until now has convinced you how important it is to take the steps you can to protect your privacy on the internet (even though most of those who took our survey said they don't take any steps). An article published by The Chronicle of Higher Education titled "Why Privacy Matters Even if You Have 'Nothing to Hide'" provides some compelling reasons. People often fall back on the mantra "if you have nothing to hide, you have nothing to fear" when faced with the reality of government surveillance. One humorous response: "If you have nothing to hide, then that quite literally means you are willing to let me photograph you naked? And I get full rights to that photograph, so I can show it to your neighbors?" It's true that the concept of "privacy" is difficult to define, but problems can quickly arise when the government collects too much personal data: George Orwell's 1984 is a notable example. Privacy isn't inherently linked with hiding "bad" things: people have a right to privacy. One day, someone could hack into a government's surver (well, it's already happened, with disastrous effects) and use that personal data against you. And who's to say we should trust the U.S. government with our data in the first place? People of color in America are already feeling the negative effects of being incorrectly/unfairly targeted by the government. When outside parties attempt to piece together the data they have collected, they often paint disorted pictures that reflect their own biases. Clearly, we must hold the U.S. government accountable for its blatant violations of the basic right to privacy. And when that doesn't work, we as users should take matters into our own hands to protect our privacy.
Concrete Steps Toward Privacy
Information from Norton, Consumer Reports, and Tech News World contributed to this list of tips.
- Use a VPN when in public spaces (and NEVER use public WiFi).
- Don't overshare on social media.
- Browse in incognito and use DuckDuckGo as your search engine.
- Check your data breach status on this website.
- Please, use different passwords for each website, and make sure those passwords aren't easy to guess.
- Enable two-factor authentication on your accounts.
- Go to the settings of every program/device you use to ensure the maximum security and privacy settings are enabled.
- Encrypt your data regularly.
- Turn off GPS tracking on your phone.
- Make sure every browser is HTTPS.
- Never give up secure data over the internet unless it really is a trusted website.
- Beware of Internet Service Providers (ISPs): most monitor your online data. This can be circumvented by getting a VPN.
- Clear your cookies regularly, and make sure websites collect as few as possible.
Even if you take all of these measures, you still won't be totally protected. Why is that? Online technologies are so ubiquitous that their breaching is inevitable. Furthermore, the government doesn't seem like they're going to stop watching us anytime soon. But don't lose hope: if we mobilize and push for reform in politics and security, we can get closer to a secure, private online world.
